Receive your JavaScript security report
More no-brainers
- CDN server security check
- 5 tips for a secure use of JavaScript libraries
- Your WordPress “may or may not” get security updates!?
- Usage of http security headers
Your WordPress “may or may not” get security updates!?
Of 65 companies that I've observed, 18 have at least one WordPress installation running. Of these 18 companies, there are 6 that run at least one server with an old version that ‘may or may not receive security updates’, according to WordPress Codex. Thus, 1 out of 10 companies uses a (potential) vulnerable WordPress server! In this article, the main security risks with WordPress are discussed and accompanied by ways to address them.
Vulnerable WordPress core
Research by internet-security-scan.com shows that 10% of organizations run a vulnerable WordPress version. That is, a version that “may or may not get security updates as serious exploits are discovered”, according to WordPress codex. When counting the servers, it turns out that 6 out of 47 WordPress servers are lacking updates. Mind that these numbers are restricted to enterprises, they don’t include private hobby-sites.
This patch gap exists despite the fact that WordPress has a convenient upgrade-mechanism for its core application in version 3.7 and higher. The uncertainty of the deployment of security patches is a weakness of many open source products, which is a different topic but something that companies should be aware of.
An excellent source for information on WordPress vulnerabilities is offered by wpvulndb. This site includes plug-in and theme-vulnerabilities. It is related to wpscan, a WordPress vulnerability scanner.
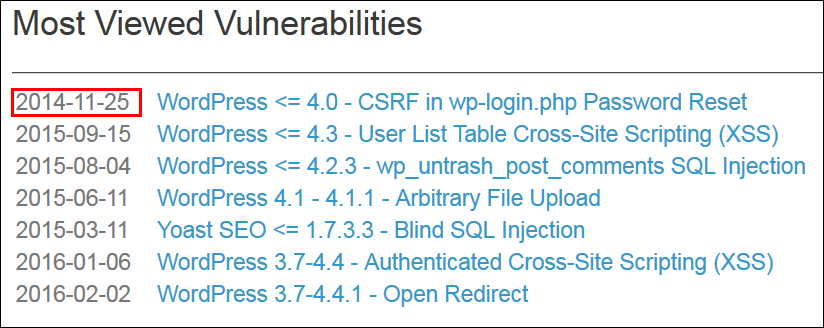
One list on vulndb.com that fascinates me is that of ‘most viewed vulnerabilities’ (see diagram below). The most viewed vulnerability is over two years old and has long been patched. Who would be interested in looking up this information about an old bug? I think that this site is not only used by defenders...
Vulnerable plug-ins
The WordPress plug-ins provide the flexibility to adapt functionality of your needs. This is one of the reasons why the platform is so popular. However, many themes and plugins are released with unknown vulnerabilities or without any security audit prior to release. As a result, they are vulnerable to attack. An interesting blog on plug-in vulnerabilities can be found here. Although a few years old, the article is still valuable.
Unfortunately, the update mechanism of the plug-ins is completely unrelated to that of the core. Each plug-in has it’s own schedule for new releases and bug-fixes, and the mechanism for deployment of patches varies as well. This makes it hard for a system administrator to stay in tune with latest security patches of plug-ins.
A generic measure to reduce the attack surface of plug-ins is to minimize the amount of installed plug-ins.
Link-spam through comments on blog
One of the annoyances of WordPress administrators are loads of bogus comments beneath every blog. These comments form a way for other websites to get back-links from your website, and several SEO-companies seem to be exploiting this possibility in order to give their clients a higher ranking in Google. The comments can also be used to launch cross-site-scripting attacks against visitors of your site.
In case that the comments need approval from the WordPress administrator before getting published, they can still be dangerous. For example, a hacker could inject malicious code in it that will be executed in the mailbox of the administrator. This way, a successful cross-site-scripting attack could lead to hijacking an administrator session in WordPress, or to the theft of admin passwords.
Plugins (such as Akismet) are available and recommended for sanitizing blog comments.
Weak administrator passwords
The admin section of a WordPress installation is often found at the /wp-admin/-directory. Usually, this directory is public available. That means that any attacker can try to guess the password and logon to the admin section.
A known attack is that the headers of the web-pages (invisible for end users) are loaded with back-links to other websites. Again, a common practice of some SEO-service providers. An other attack could be to steal credentials or other sensitive information from visitors, or to attack the visitors browser with zero-day exploits and compromise them.
The remedy is to choose strong passwords that are not easy to guess. It’s also safer when access to admin-functionality is restricted to specific IP-addresses. This reduces the attack surface drastically.
Dependency on JavaScript libraries
WordPress core as well as plug-ins frequently make use of public-domain JavaScript libraries, such as jQuery. These libraries have their own security patches and they exist in many versions. A common security issue with JavaScript is the possibility for Cross-Site-Scripting, possibly leading to theft of sensitive data or passwords. More on JavaScript library security can be found in this article. The remedy is to check (and upgrade) the JavaScript library versions, aside from checking the WordPress core and plugin versions.
Conclusion
The flexible and cheap WordPress content management system needs security attention during installation and operation.
- Good hardening guidelines for installing Wordpress securely can be found in the Codex.
- A quick scan to verify the broader security of the server can be done with internet-security-scan
- Proper patch management of WordPress and plug-ins is key. Keep checking wpvulndb.com and run wpscan on a regular basis.